Update May 2025 - Technical Snapshot
Our update on how the Fata Morgana team (Defence and National Security, Turing) catalyses a paradigm shift in cyberdefence for critical national infrastructure.
One of the core missions of the Alan Turing Institute, under the Defence and National Security Grand Challenge, is to address the growing threats to critical national infrastructure (CNI).
These risks are accelerating not just due to increasingly sophisticated adversaries, but because those adversaries are now using artificial intelligence to scale their operations (e.g., automating reconnaissance, vulnerability discovery, and exploitation) at a pace human teams struggle to match. While much of the current discourse revolves around matching or outpacing attackers in the development of dual-use AI capabilities, the Fata Morgana team is deliberately exploring approaches that disproportionately benefit defenders with very limited plausible offensive use. This isn’t just a moral stance; it’s a strategic one. By working on single-use defensive applications, we aim to shift the cyber risk equilibrium in a direction that favours resilience over escalation.
In this first update, we share how we out-innovate infrastructure malware by making defence cheaper, faster, and smarter. We’ve created a solution designed specifically for the complexity of industrial infrastructure. Our solution uses dynamic emulation environments to deceive malware into revealing itself, without it ever touching real cyber-physical hardware. We are building systems that fluently mimic common and obscure, undocumented protocols without requiring exhaustive reverse engineering or human analysis effort. This is not an incremental improvement; it's a strategic effort using AI to shift the balance of power toward defenders by enriching tooling and scaling defences.
Critical Infrastructure Cyber Security: A Perfect Storm
Critical infrastructure is increasingly exposed to cybersecurity threats that are uniquely difficult to manage. The sector combines high stakes with an exceptionally challenging security environment. Many systems were not designed with modern threats in mind, yet they are now networked, dependent on legacy equipment, and operated by organisations with limited resources and often without dedicated cybersecurity personnel.
Security across these environments is highly uneven. Infrastructure operators rely on equipment from multiple vendors, each with its own security features, firmware, and configuration requirements. Even where air-gapping was once a plausible defence, remote access and digitisation have eroded these protections. Meanwhile, traditional IT security tools struggle to adapt to the bespoke nature of OT (operational technology) environments, making it difficult to deploy generic detection or prevention solutions.
We are working to introduce targeted, high-impact interventions that do not merely incrementally improve defences but shift the underlying dynamics substantially in favour of defenders.
A New Paradigm for OT Threat Detection and Analysis
Our first target is a growing threat: malware and tools designed specifically for operational technology environments. Unlike generic IT malware, these tools target physical systems by exploiting specialised hardware, firmware, and industrial protocols. OT malware is typically designed to target a specific deployment, making broad, scalable analysis very difficult.
Current defensive tooling, including digital twins, struggles to generalise against this attack vector, as they seek to replicate (with high fidelity) a narrow range of known devices and typically require manual engineering. As a result, they scale poorly, are expensive to build, and are slow to adapt to new threats.
Our approach is fundamentally different. Instead of replicating specific devices, we create responsive environments that adapt in real-time to the malicious behaviour (e.g., malware activity). These environments are underpinned by AI models that learn how to generate protocol-compliant responses, even when documentation is incomplete or non-existent. The goal is not perfect replication, but sufficient fidelity to elicit and observe the malware’s intended effect.
Who Benefits and How
Our solution is designed primarily for security researchers, critical infrastructure operators, and national cybersecurity agencies. These stakeholders will use the system to:
Safely analyse OT malware behaviour without risking real infrastructure
Identify attack patterns and develop targeted countermeasures
Gather threat intelligence on emerging OT malware families
Train security teams to recognize and respond to OT-specific attacks
By providing a low-cost, rapidly deployable alternative to hardware-based and simulation-based testing environments, our approach democratizes OT security research and enables faster response to evolving threats.
Our Solution: Smoke and Mirrors
Rather than emulating specific devices, we're developing AI models that adapt in real-time to malware behaviour. These models simulate OT hardware by convincingly speaking whatever protocol the malware probes for, even when undocumented. This is sufficient where malware is pivoting from a traditional IT device to the OT environment over the network, which is the predominant attack vector. This creates a dynamic, convincing environment that holds malware in place, revealing its behaviour without exposing real infrastructure to risk.
Use Case: Analysing Industrial Protocol Malware
Consider a scenario where a security researcher receives a suspicious file believed to target Rockwell Automation’s Micrologix PLCs. Traditionally, analysing this sample would require access to these specific controllers i.e., hardware that costs hundreds of pounds and requires specialised knowledge to configure properly. With Smoke and Mirrors, the analyst can simply:
Spin up a virtual OT environment
Execute the suspicious file in a sandboxed environment
Allow it to scan the network, where it discovers what appears to be Micrologix devices
Analyse the malware’s attempts to communicate with those devices
Behind the scenes, our AI-powered responders interact with the malware, generating accurate protocol responses that mimic authentic Micrologix PLCs. The malware is deceived into “believing” it's communicating with real devices, causing it to reveal its payloads, command-and-control mechanisms, and exploitation techniques.
The analyst can observe the entire attack chain without any risk to actual infrastructure. The system compiles a report with how the malware attempts to manipulate industrial processes, which configuration settings it targets, and what its ultimate objective appears to be. This intelligence can then be shared with industrial operators and security vendors to develop effective countermeasures or assess their risk.
Technical Implementation
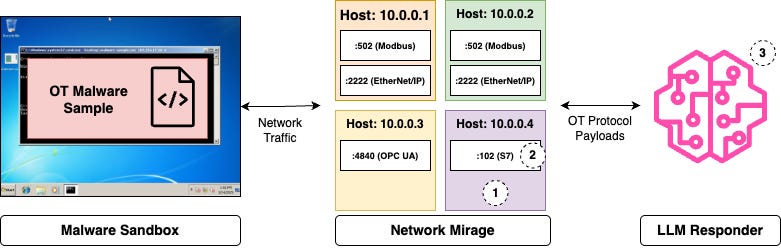
Our implementation uses a lightweight proxy architecture that intercepts malware communication attempts and routes them to our AI models. The models analyse communication patterns in real time and generate appropriately formatted responses that mimic legitimate OT devices. The system maintains internal state to ensure consistency across interactions, creating the illusion of a persistent hardware environment. This allows for scalable deployment across diverse protocol environments without requiring protocol-specific engineering for each new target.
The system comprises several components:
Network Manager: Intercepts network traffic using Scapy to capture ARP and TCP SYN packets. It dynamically allocates IPs to create a virtual network environment for malware interaction.
Host System: Manages virtual hosts with their own IP addresses and runs multiple TCP services across different ports, creating a convincing network topology for malware to explore.
Protocol Classification System: Identifies communication protocols (currently supporting Modbus TCP ) through a flexible, extensible classification framework.
Responder Framework: Provides protocol-specific responses to malware queries through various responding agents including the Echo Responder, the Lookup Responder, and an LLM Responder.
AI Misuse & Next Steps
Much of the current discussion around AI in cybersecurity centres on preventing dual-use misuse. Our work instead focuses on building tools with no offensive utility at all; systems that only help defenders and cannot be trivially re-purposed to conduct attacks. This approach enables open collaboration without amplifying risk and contributes to a safer overall research ecosystem. However, we recognise the need to also advance potentially sensitive areas to stay ahead of emerging threats.
From a technical perspective, our focus now shifts to scaling our approach. We're exploring more efficient, protocol-specialised models for broader deployment across multiple industrial protocols, to enable a comprehensive defence system capable of engaging with a wide range of OT attack tools and malware variants.
Project Access
You can access the sanitised project code here. This is the demo code, mostly in Jupyter notebooks for ease of use. If you require access to the full codebase, please get in touch.